
5 Warning Signs Your Vendor Compliance Process Is Putting You at Risk
Identify critical gaps in your vendor compliance process before they lead to serious consequences.
The Hidden Risks in Vendor Compliance: Early Warning Signs
In today's interconnected and increasingly complex business environment, organizations rely heavily on a vast ecosystem of third-party vendors. While these partnerships are essential for driving innovation, expanding capabilities, and achieving operational efficiencies, they also introduce a significant layer of risk. Vendor compliance issues, if left unaddressed, can quickly escalate into substantial threats, impacting not just financial stability but also regulatory standing, operational continuity, and, perhaps most critically, reputational integrity. It's not enough to simply have a vendor compliance program in place; vigilance is paramount in identifying the subtle, yet critical, early warning signs that indicate potential compliance failures. These signs often point to deeper systemic issues that, if ignored, can lead to severe consequences, including hefty fines, data breaches, service disruptions, and irreversible damage to your brand.
Recent studies consistently underscore the criticality of robust vendor oversight. For instance, industry analyses reveal that as much as 65% of compliance violations can be traced back to inadequate vendor management and oversight. This alarming statistic highlights just how crucial it is to move beyond superficial checks and adopt a truly proactive approach to risk detection. Many organizations operate under the mistaken belief that simply having contracts in place or conducting annual reviews is sufficient. However, the dynamic nature of today's regulatory landscape and the sophistication of cyber threats demand continuous monitoring and an acute awareness of the subtle indicators that your vendor compliance process might be falling short. Recognizing these warning signs early can be the difference between proactive mitigation and reactive crisis management, safeguarding your organization from avoidable and potentially devastating outcomes. This detailed guide aims to equip you with the knowledge to spot these red flags before they become major problems.
The implications of vendor non-compliance extend far beyond direct financial penalties. Consider the ripple effects: a vendor's data breach could expose sensitive customer information, leading to massive legal liabilities and a loss of customer trust. A vendor's failure to adhere to environmental regulations could trigger significant public relations crises and boycotts. Or, a vendor's operational instability could disrupt your supply chain, halting production and impacting your ability to deliver services. The interconnectedness of modern supply chains means that a vulnerability in one vendor can quickly become a systemic risk for your entire organization. Therefore, understanding and addressing these warning signs is not merely a compliance exercise; it is a fundamental aspect of comprehensive enterprise risk management and maintaining business resilience in a competitive and highly regulated world. We will now delve into five specific warning signs that demand your immediate attention.
Warning Sign 1: Inconsistent Documentation Management
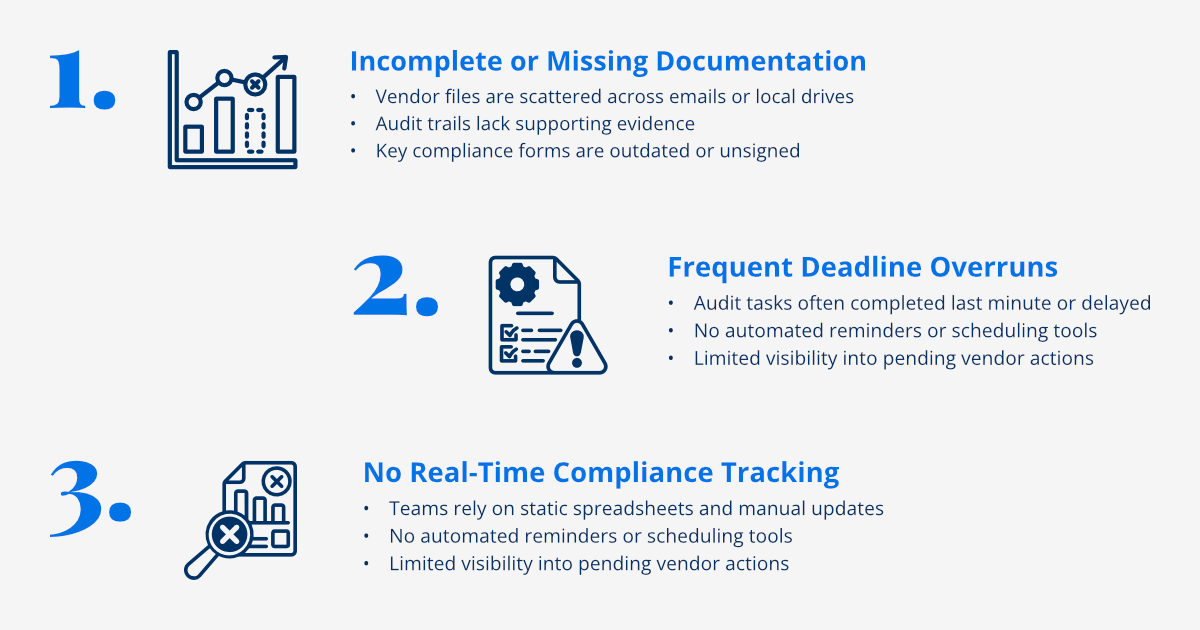
One of the most immediate and telling red flags for a struggling vendor compliance process is inconsistent documentation management. When critical vendor documentation is scattered across disparate systems, stored in multiple locations, or exists in various unmanaged versions, it's a clear indication of deeper systemic issues. This seemingly administrative problem can have profound implications, making it incredibly difficult to maintain a complete, accurate, and readily auditable trail of compliance activities. This lack of centralized and controlled documentation hinders your ability to quickly retrieve necessary information, slows down audit responses, and significantly increases the risk of overlooking critical data points that could expose your organization to non-compliance.
Document Scattering
Critical vendor documents, such as contracts, service level agreements (SLAs), compliance certificates, audit reports, and cybersecurity attestations, being stored across multiple systems or physical locations, makes it incredibly difficult to maintain a complete and cohesive audit trail. This fragmentation leads to a significant administrative burden and increases the risk of overlooking crucial information or misplacing essential records, hindering your ability to present a unified view of vendor compliance during internal or external audits. It's like trying to solve a puzzle when half the pieces are missing or in different boxes.
Version Control Issues
The proliferation of multiple versions of the same document without clear and consistent tracking of the most current and approved version is a critical vulnerability. This can lead to compliance teams referencing outdated agreements, performing assessments based on incorrect information, or failing to identify when a vendor's documentation has expired or been revoked. Without robust version control, the integrity of your compliance data is compromised, opening the door to non-compliance based on outdated or incorrect information. This chaos can quickly undermine the reliability of your entire compliance program.
Addressing inconsistent documentation management is foundational to a strong vendor compliance program. Implementing a centralized, automated document management system with robust version control and clear audit trails is not just a best practice; it's a necessity for ensuring accuracy, efficiency, and defensibility in your compliance efforts. This initial step can unlock significant improvements across your entire vendor risk management strategy.
Warning Sign 2: Delayed Risk Assessments
Another critical warning sign that your vendor compliance process is putting you at risk is the presence of consistently delayed or infrequent risk assessments. In a fast-evolving threat landscape, manual risk assessment processes are often inherently slow, creating dangerous compliance gaps and leaving your organization vulnerable to emerging threats. The world changes quickly, and risks associated with vendors do too. If your assessment process can't keep pace, you're operating with outdated information, which is almost as dangerous as having no information at all.
- Extended Assessment Time: If your vendor risk assessments are taking weeks or even months to complete, it's a serious problem. During such prolonged periods, new vulnerabilities can emerge, a vendor's financial stability could shift, or their cybersecurity posture might degrade. This leaves your organization exposed to threats that have developed since the assessment began, or even since the last assessment was completed. The goal should be to conduct assessments with speed and agility, reflecting the dynamic nature of risk.
- Inconsistent Evaluation: Manual risk assessment processes often rely on individual assessors' judgment, leading to different individuals applying varying standards or interpretations. This inconsistency results in subjective and unreliable risk ratings. One assessor might deem a risk low, while another might identify it as high, leading to a fragmented and unreliable overall risk profile. Without standardized, objective criteria consistently applied, you lack a true, comparable understanding of your vendor risk landscape across your entire portfolio.
- Delayed Remediation: Even if critical issues are identified during an assessment, reliance on manual review processes can lead to significant delays in addressing them promptly. The time it takes to review findings, assign responsibilities, track remediation efforts, and verify their completion can be extensive. During this lag, identified vulnerabilities remain open, potentially causing actual breaches or compliance failures. The effectiveness of risk identification is severely undermined if remediation is not swift and decisive.
These delays and inconsistencies in risk assessment directly translate into heightened organizational exposure. Modern solutions leverage automation and artificial intelligence to conduct faster, more consistent, and continuous risk assessments, ensuring that your risk profile is always current and actionable. Proactive risk management is not just about identifying risks, but about addressing them with speed and precision, something manual processes struggle to deliver.
Warning Sign 3: Inadequate Audit Trail
A robust and comprehensive audit trail is the backbone of any effective compliance program. Without it, organizations struggle significantly to demonstrate due diligence and adherence to regulatory requirements during internal reviews, external audits, or, critically, in the event of a breach or non-compliance incident. An inadequate audit trail isn't just an administrative inconvenience; it's a critical vulnerability that can expose your organization to severe penalties and reputational damage. It's like having to prove you did something without any evidence to back it up.
Incomplete Records
When there's missing or incomplete documentation of crucial compliance activities, decisions, and communications, it becomes nearly impossible to paint a full picture of your due diligence efforts. This includes records of risk assessments conducted, issues identified, remediation plans implemented, and communications with vendors regarding their compliance status. Regulators and internal auditors will demand a complete and verifiable history. Gaps in this record can raise serious questions about your organization's commitment to compliance and its ability to manage vendor risks effectively.
Manual Tracking
Over-reliance on manual tracking methods for compliance activities, such as spreadsheets or disparate email threads, is highly prone to errors, inconsistencies, and omissions. Human fallibility means that important details can be overlooked, records might not be updated in real-time, or vital communications could be lost. This compromises the integrity and reliability of the audit trail, making it difficult to reconstruct events accurately or prove that specific compliance steps were taken at a given time. Such manual dependencies can create significant headaches during an audit, potentially leading to adverse findings.
To mitigate these risks, organizations must implement automated systems that capture every action, decision, and communication related to vendor compliance in a centralized, immutable, and easily accessible format. A robust, automated audit trail provides irrefutable evidence of your compliance efforts, significantly reducing the burden of audit preparation and instilling confidence in your overall risk management framework. This transparency and traceability are essential for demonstrating accountability and mitigating potential legal and financial repercussions.
Warning Sign 4: Inadequate Vendor Monitoring
One of the most critical and often overlooked warning signs of a vulnerable vendor compliance process is inadequate or infrequent vendor monitoring. It's a common misconception that once a vendor is onboarded and an initial risk assessment is complete, the job is done. However, vendor risk profiles are not static; they can change rapidly due to shifts in the vendor's financial health, cybersecurity posture, operational stability, or even the regulatory landscape itself. Infrequent vendor reviews or a lack of real-time monitoring capabilities mean your organization is operating with outdated information, missing critical compliance issues as they emerge, and thereby exposed to significant and evolving risks that could have been mitigated if detected earlier.
- Annual Reviews Only: Relying solely on annual reviews for vendor compliance is a dangerous practice. In today's dynamic threat environment, a vendor's cybersecurity controls could be compromised, or their financial stability could deteriorate significantly in a matter of weeks, not months. Waiting for an annual review means you are operating with an outdated risk assessment for the vast majority of the year, missing critical changes in vendor risk profiles that could impact your organization immediately. This reactive approach is inherently insufficient for proactive risk management.
- Limited Visibility: A lack of real-time or near real-time monitoring capabilities means you have limited visibility into your vendors' ongoing compliance and risk posture. You might not be immediately aware of changes in their certifications, a new data breach affecting them, or a change in their legal status that could impact your contractual agreements. This results in delayed detection of compliance issues, preventing timely intervention and leaving your organization vulnerable to escalating risks that could have been mitigated if detected earlier.
- Inconsistent Monitoring: Applying different monitoring approaches or levels of scrutiny to different vendors without a clear, risk-based methodology can lead to significant gaps in oversight. High-risk vendors might not receive the continuous monitoring they require, while low-risk vendors might consume disproportionate resources. This inconsistency means your compliance efforts are not optimally allocated, leaving certain areas of your vendor ecosystem inadequately managed and increasing overall enterprise risk.
To truly safeguard your organization, vendor monitoring needs to be continuous, comprehensive, and risk-aligned. Leveraging automated solutions that provide real-time alerts, continuous data feeds, and dynamic risk scoring can transform your vendor monitoring from a periodic chore into a proactive and intelligent defense mechanism. This ensures that you always have an up-to-date understanding of your vendor risk landscape and can respond swiftly to any emerging threats or compliance deviations.
Warning Sign 5: Manual Process Dependencies
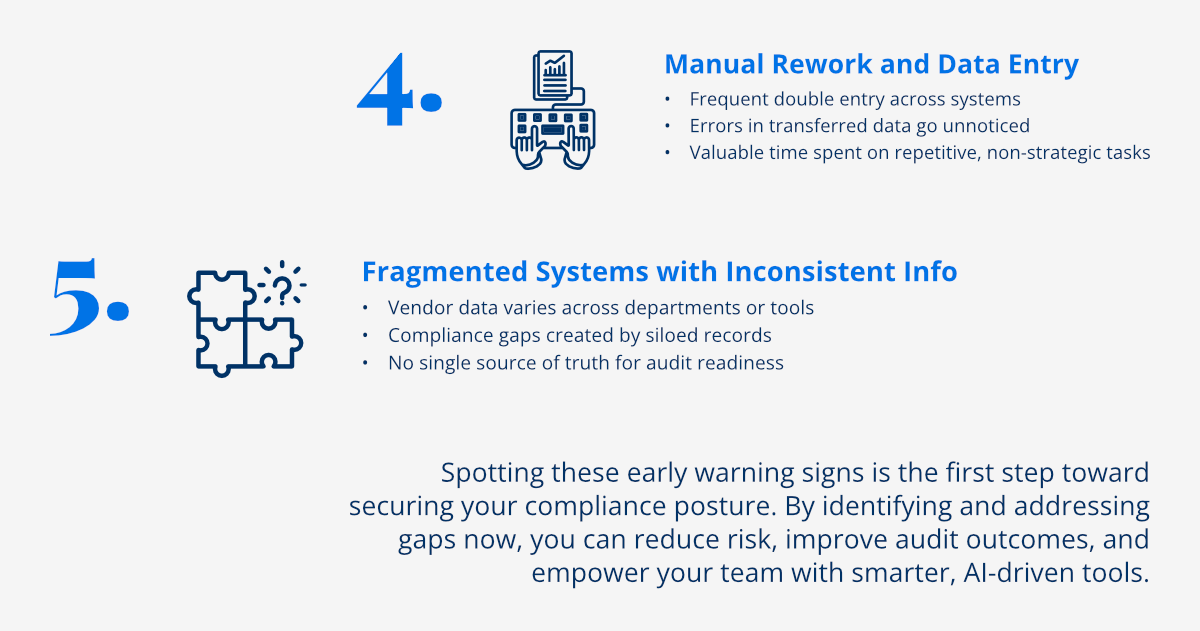
The fifth, and perhaps most pervasive, warning sign that your vendor compliance process is putting you at risk is an over-reliance on manual processes. While human judgment is invaluable in certain aspects of compliance, performing repetitive, data-intensive tasks manually significantly increases the risk of human error and creates bottlenecks that can lead to critical compliance failures. Manual dependencies are the antithesis of efficiency and scalability in modern compliance management, turning a proactive function into a reactive burden.
Error-Prone Processes
When compliance teams are burdened with manual data entry, processing, and cross-referencing vast amounts of vendor information, the risk of errors and inconsistencies skyrockets. Simple typos, overlooked details, or incorrect data transcription can lead to inaccurate risk assessments, flawed compliance reports, or missed deadlines. These errors can have severe consequences, from regulatory fines to misinformed strategic decisions, all stemming from the inherent fallibility of human manual processing. Automation eliminates these common sources of error.
Scalability Issues
As your organization grows and its vendor portfolio expands, manual processes quickly become unsustainable. The time and resources required to manage compliance for an increasing number of vendors will grow exponentially, leading to bottlenecks, delays, and an inevitable decrease in the quality of oversight. Manual processes simply cannot keep pace with increasing compliance requirements or the complexities of a growing global supply chain. This lack of scalability means that as your business succeeds, your compliance function risks becoming a bottleneck, potentially hindering further growth.
The solution to manual process dependencies lies in strategic automation. By leveraging AI-powered platforms and automated workflows, organizations can eliminate repetitive tasks, significantly reduce human error, and ensure that their compliance processes are scalable, efficient, and consistently applied. This shift not only mitigates significant risk but also frees up highly skilled compliance professionals to focus on higher-value activities that require their expertise, such as complex risk analysis, strategic policy development, and stakeholder engagement.
Conclusion: Taking Action on Warning Signs
Recognizing these five warning signs—inconsistent documentation, delayed risk assessments, inadequate audit trails, insufficient vendor monitoring, and over-reliance on manual processes—is the crucial first step toward building a truly robust and resilient vendor compliance framework. Ignoring these indicators can lead to significant and potentially catastrophic consequences for your organization, ranging from substantial financial penalties and legal liabilities to severe reputational damage and operational disruption.
The good news is that these risks are not insurmountable. By proactively addressing these warning signs through the strategic adoption of modern technologies, organizations can transform their vendor compliance processes from reactive and vulnerable to proactive and secure. Implementing AI-powered solutions and automated monitoring systems is key to this transformation. These advanced platforms can centralize documentation, accelerate and standardize risk assessments, create immutable and comprehensive audit trails, enable continuous real-time vendor monitoring, and eliminate error-prone manual dependencies.
The ultimate goal is to shift your organization's posture from merely reacting to compliance demands to actively anticipating and mitigating risks. By embracing intelligent automation, you can ensure continuous compliance, enhance your overall risk posture, and safeguard your organization's future in an increasingly complex and regulated business landscape. This strategic investment in compliance technology is not just about avoiding penalties; it's about building a foundation of trust, resilience, and sustainable growth for your entire enterprise.